Use Cases and Case Studies
The UID Protocol in IDCHAIN is designed for various real-world application scenarios that require secure, verifiable, and efficient digital identities. Here are some key case studies illustrating how the UID Protocol can be applied across different sectors.
1. Interaction with DApps through e.id
- Scenario
Users want to interact with decentralized applications (DApps) in the IDCHAIN ecosystem using their digital identity. -
Process
1. Downloading and Installing e.id Wallet- Users download the e.id Wallet application from the app store or access the web version.
- After installation, users create an account and generate an identity address using the e.id domain.
2. Integration with DApps
- Users select the DApps they want to access and connect them with the e.id Wallet.
- The e.id Wallet manages and sends the user's UID to the selected DApps.
3. Interaction and Transactions
- Users can perform transactions or other interactions with the DApp using their UID.
- All interactions are recorded on the IDCHAIN blockchain, ensuring transparency and security.
-
Benefits
- Ease of Use: Simplifies the process for users to manage and utilize their digital identities across various DApps.
- Security: Utilizes blockchain technology to ensure the integrity and security of identity data.
- User Control: Users have full control over their UID and how it is used within the DApps ecosystem.
2. Identity Verification for Financial Services
- Scenario
Banks or financial institutions require customer identity verification to open accounts or access financial products. -
Process
1. Registration on the Financial Platform- Users access the banking platform through an app or website.
- The user's UID is sent via the e.id Wallet application.
2. Identity Verification
- The banking platform sends a request to the Verifier to validate the user's UID.
- The Verifier checks the UID against the data recorded on the IDCHAIN blockchain.
3. Providing Service Access
- If the UID is valid, the user is granted access to financial services such as opening an account, applying for a loan, or using a credit card.
-
Benefits
- Efficiency: Speeds up the identity verification process.
- Security: Reduces the risk of identity theft.
- Privacy: No physical documents need to be shared.
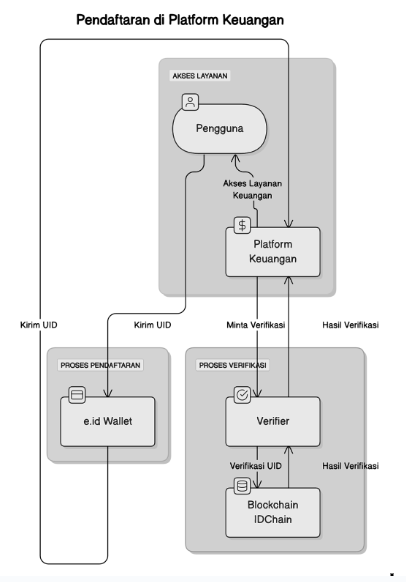
Explanation Flowchart::
- Registration on the Financial Platform
- Description: Users register on a financial services platform (e.g., a digital bank) using their e.id Wallet. At this stage, users provide their UID for verification purposes.
- Relation:
- Description: Users register on a financial services platform (e.g., a digital bank) using their e.id Wallet. At this stage, users provide their UID for verification purposes.
- Identity Verification by the Financial Platform
- Description: The financial platform receives the UID from the user and sends a request to the Verifier to perform verification through the IDCHAIN blockchain.
- Relation:
- Financial Platform → Verifier: The verification request is sent to the Verifier.
- Verifier → IDCHAIN Blockchain: The Verifier verifies the authenticity of the UID by matching it against the blockchain.
- Description: The financial platform receives the UID from the user and sends a request to the Verifier to perform verification through the IDCHAIN blockchain.
- Access to Financial Services
- Description: After successful verification, users are granted full access to financial services, such as opening an account, accessing credit products, or conducting transactions.
- Relation:
- Financial Platform → User: Users receive access to financial services after successful verification.
- Financial Platform → User: Users receive access to financial services after successful verification.
- Description: After successful verification, users are granted full access to financial services, such as opening an account, accessing credit products, or conducting transactions.
3. Digital Election System
-
Scenario
The government or organization uses a digital election system that requires a unique identity for each voter. -
Process
1. Voter Registration- Each voter is assigned a unique UID through an official application.
- The UID is recorded on the blockchain to ensure that each person can only register once.
2. Voting
- Voters use their UID to access the digital election system.
- Their votes are recorded and verified without revealing their personal identity.
3. Vote Counting
- The blockchain ensures that all votes are legitimate and that there are no duplicates.
-
Benefits
- Transparency: Each vote can be traced without revealing the voter's identity.
- Security: UID prevents identity fraud.
- Efficiency: Reduces the time needed for manual vote counting.
4. Access to Public Services
-
Scenario
The government provides digital health services that require identity verification of citizens. -
Process
1. Service Request- Citizens submit a request for health services through the official government application.
- Their UID is sent via the e.id Wallet application.
2. Identity Verification
- Government agencies verify the user's UID against the data on the IDCHAIN blockchain.
- If valid, citizens are granted access to services such as doctor consultations or medication pickup.
3. Provision of Services
- Services are provided without the need to carry physical documents.
-
Benefits
- Ease of Access:: Services can be accessed quickly, especially in remote areas.
- Security: Citizens' identities are protected by the blockchain.
- Operational Efficiency: Reduces manual administrative costs.
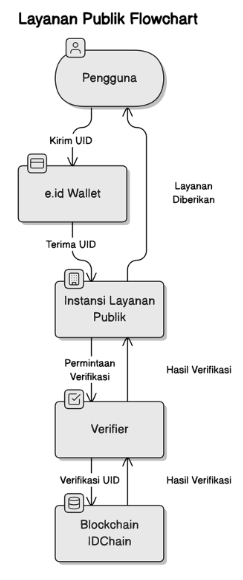
Explanation Flowchart::
- Request for Access to Public Services
- Description: The user wants to access public services, such as healthcare or population administration. The user provides their UID through the e.id Wallet to the relevant agency.
- Relation:
- Description: The user wants to access public services, such as healthcare or population administration. The user provides their UID through the e.id Wallet to the relevant agency.
- Identity Verification by the Public Agency
- Description: The public service agency receives the user's UID and performs verification by sending a request to the Verifier. The Verifier then verifies the UID through the IDCHAIN blockchain.
- Relation:
- Public Service Agency → Verifier: The verification request is sent to the Verifier.
- Verifier → IDCHAIN Blockchain: The Verifier uses the blockchain to verify the UID.
- Description: The public service agency receives the user's UID and performs verification by sending a request to the Verifier. The Verifier then verifies the UID through the IDCHAIN blockchain.
- Provision of Public Services
- Description: After successful verification, the public agency provides the services required by the user. For example, the user may receive healthcare services or obtain administrative documents.
- Relation:
- Public Service Agency → User: The user receives public services after successful verification.
- Public Service Agency → User: The user receives public services after successful verification.
- Description: After successful verification, the public agency provides the services required by the user. For example, the user may receive healthcare services or obtain administrative documents.
5. Management of Academic Certificates
-
Scenario
Universities use UID to issue verifiable digital graduation certificates. -
Process
1. Certificate Issuance- The university records the graduation certificate as a Verifiable Credential associated with the student's UID.
2. Certificate Validation
- Potential employers or other institutions can verify the authenticity of the certificate directly through the IDCHAIN blockchain.
3. Use of Certificates
- Students can use their certificates to apply for jobs or continue their education without the risk of forgery.
-
Benefits
- Security: Digital certificates cannot be forged.
- Ease of Validation: The verification process is simple and instant.
- Operational Efficiency: Certificates can be accessed and verified anywhere.