How the UID Protocol Works in IDCHAIN
Concept
The UID (Universal Identifier) Protocol in IDCHAIN is a blockchain-based identification system that enables the secure and efficient creation, management, and verification of digital identities. UID leverages the W3C Decentralized Identifier (DID) standard, ensuring interoperability and reliability across various platforms.
Key Principles of the DID Protocol
- User Sovereignty
Users have full control over their identities, including who can access their data and for what purposes. - High Security
By utilizing advanced encryption algorithms such as Blake2b, the UID Protocol guarantees the integrity and security of identity data. - Interoperability
Supporting the W3C Decentralized Identifier (DID) standard, this protocol ensures that UIDs can be used across various digital platforms and applications. - Transparency and Accountability
All changes or access to UID data are recorded on the IDCHAIN blockchain, providing an immutable digital trail.
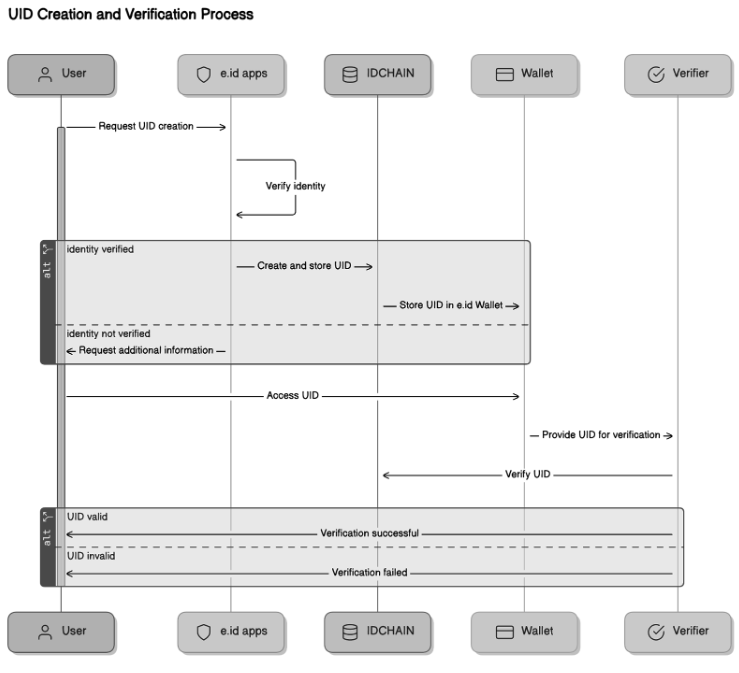
Diagram Explanation:
-
User Requests UID Creation:
The user, through an application like e.id, requests the creation of a new UID. This process begins when the user registers their identity for a specific purpose. -
Identity Verification by the Issuer (e.id application):
The user's identity information is verified by the issuer (e.id application), which can be a trusted institution. This verification process may include KYC (Know Your Customer). - UID Creation and Storage in IDCHAIN:
After successful verification, the issuer will create a unique UID for the user. This UID uses the DID standard and is then stored on the IDCHAIN blockchain to ensure the integrity and security of the data. - UID Available to Users Through e.id:
Once the UID creation is complete, the UID is stored in the e.id application with the help of the e.id wallet or third-party applications used by the user. The user now has full control over their digital identity. - Using UID to Access Services:
Users can use their UID to access services that require identification, such as financial or government services. The UID can be presented to third parties for verification. - Verification Process by the Verifier:
The verifier (the party verifying the identity) receives the UID and verifies its validity through the IDCHAIN blockchain. This process involves matching the UID with existing records on the blockchain to ensure the authenticity of the identity. - Verification Results:
The verifier provides the verification results to the user or the requesting party. If the verification is successful, the service can be accessed. If it fails, the user is asked to take further steps.
Key Component
The UID Protocol consists of several key components that interact with each other to support digital identity management:
-
UID Subject
- The entity (individual or organization) identified by the UID.
- Example: A user of a financial service requiring identity verification.
-
UID Controller
- The entity responsible for creating, managing, and updating the UID.
- Example: A government agency or the e.id application.
-
UID Document
- A JSON-LD formatted document that stores UID metadata, such as public keys and relationship information.
- This document serves as a "digital passport" containing information about the UID Subject.
-
Verifiable Credential (VC)
- A digital proof that can be verified to support specific claims (e.g., organizational membership or work license).
- Stored on the blockchain to ensure security and transparency.
-
e.id Wallet
- A digital wallet that allows users to store and manage their UIDs and credentials.
- The primary tool for users to interact with the UID protocol.
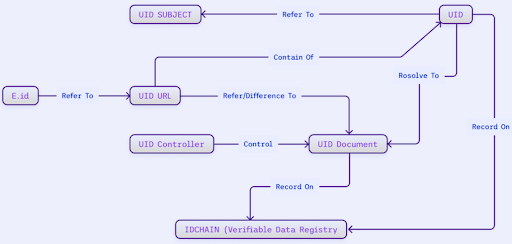
Diagram Explanation:
-
UID Subject
- The entity (individual or organization) identified by the UID.
-
UID Controller
- The entity responsible for creating, managing, and updating the UID.
-
UID Document
- A JSON-LD formatted document that stores information related to the UID, including metadata and relationships with other entities.
-
Verifiable Credential (Blockchain IDCHAIN)
- The IDCHAIN blockchain that serves as a registry for verified data for the UID. The blockchain ensures that the UID can be verified by third parties without revealing sensitive details.
-
e.id Wallet
- A digital wallet that allows users to store and manage their UIDs and credentials.
Workflow of the UID Protocol
The UID Protocol includes various steps from creation to verification of the UID. Here is the complete workflow:
-
UID Creation
- The user (UID Subject) initiates the process by submitting a request for UID creation through an application like e.id.
- The information entered by the user, such as name or other identity data, is verified by the UID Controller.
-
Data Verification by UID Controller
- The UID Controller verifies the authenticity of the user's data. This process may involve document checks or other authentication methods.
- If the verification is successful, the UID Controller creates a unique UID based on the user's information.
-
Recording UID on the Blockchain
- The created UID is recorded on the IDCHAIN blockchain. This process ensures that the UID is immutable and transparent for verification.
-
UID Distribution
-
Using UID for Verification
- Users can use their UID to access services that require identity verification, such as banks, public services, or e-commerce platforms.
-
Verification Process by Verifier
- The verifier (the party verifying the identity) checks the user's UID through the blockchain to ensure its authenticity and validity.
- If valid, the verifier grants approval, and the user can access the service.
-
Verification Results
- The verifier provides the verification results to the user or the requesting party. If the verification fails, the user is asked to update their data or complete additional steps.
Steps to Get UID
The process of getting a UID (Universal Identifier) in IDCHAIN involves several simple steps, designed to be accessible for both non-technical and technical users. Here are the steps:
-
User Registration through e.id
- Users begin by creating an account in the e.id application.
- The basic information required includes name, email, and additional identification as needed by the application.
-
Identity Verification by UID Controller
- The UID Controller receives the user data and performs verification. This process includes checking identity documents or other authentication methods such as KYC (Know Your Customer).
- If the user data is valid, the process proceeds to the next step.
-
UID Creation on the IDChain Blockchain
- After successful verification, the UID Controller creates a unique UID for the user using hashing algorithms like Blake2b.
- The generated UID is then recorded on the IDChain blockchain to ensure security and transparency.
-
Distribution of UID to Users
- The UID that has been recorded on the blockchain will be distributed back to the user through the e.id Wallet application.
- Users now have full control over their UID and can use it for digital identity purposes.
-
Using the UID
- Users can use their UID to access digital services, verify their identity, or prove specific claims.
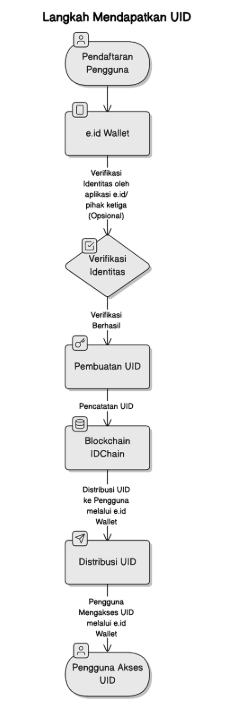
Flowchart Explanation:
-
User Registration through e.id or Third-Party Applications
- The user initiates the process by registering through e.id or third-party applications integrated with IDCHAIN. At this stage, the user enters basic information such as name, email, and other data required according to the application's needs.
-
UID Creation by UID Controller
- After successful verification, the UID Controller will create a unique UID for the user. This process is carried out using cryptographic hashing algorithms to ensure the uniqueness of the UID.
-
Recording UID on the IDCHAIN Blockchain
- The created UID is then recorded on the IDCHAIN blockchain. This recording ensures that the UID is secure and immutable, thus maintaining the integrity and transparency of the user's digital identity.
-
Distribution of UID to Users through e.id Wallet
- Once the UID is recorded on the blockchain, it is distributed to the user through the e.id Wallet. The user then has full control over their UID, which is stored in the digital wallet.
-
Users Access UID through e.id Wallet
- Users can now access their UID through the e.id Wallet. The UID can be used for identity verification or other purposes, such as accessing digital services that require authentication.
Steps to Create UID Document Schema
Here are the steps that the UID Controller must take to create the UID Document Schema, starting from UID creation to the verification process by the IDCHAIN blockchain.
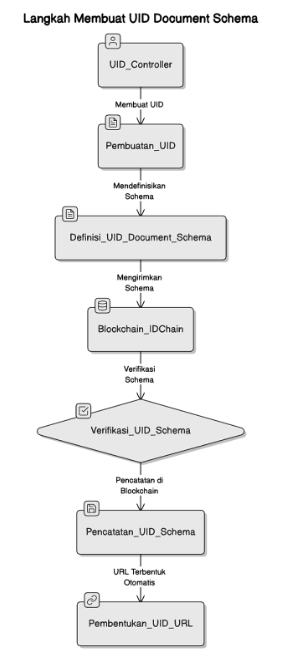
Flowchart Explanation:
-
UID Creation by UID Controller
- Description: The UID Controller initiates the process by creating a unique UID for the user. This UID is used as the primary identifier in IDCHAIN.
- Visual Representation: A box labeled "UID Controller" is connected with an arrow pointing to "UID Creation," indicating that the first step is the creation of the UID.
-
Definition of UID Document Schema
- Description: After the UID is created, the UID Controller defines the UID Document Schema. This schema contains the requirements and structure of the metadata desired by the UID Controller, such as basic identity information, relationships with other entities, and UID details.
- Visual Representation: An arrow from "UID Creation" to "Definition of UID Document Schema" shows the step for defining the metadata structure.
-
Submission of UID Document Schema to Blockchain for Verification
- Description: The UID Controller submits the UID Document Schema to the IDCHAIN blockchain for verification. The verification process ensures whether the schema has been created before and whether the UID Controller has the rights to create this schema.
- Visual Representation: An arrow from "Definition of UID Document Schema" to "IDCHAIN Blockchain" indicates the submission of the schema for the verification process.
-
Verification and Recording of UID Document Schema by the Blockchain
- Description: The IDCHAIN blockchain verifies the UID Document Schema. The blockchain checks whether the schema has been created before and whether the UID Controller is authorized to create this schema. If the verification is successful, the schema is immediately recorded on the blockchain. Once stored, a UID Document URL is automatically generated, allowing for future access and reference.
- Visual Representation: A box labeled "IDCHAIN Blockchain" is connected to "Verify UID Schema," which continues with automatic recording. There is no manual process for generating the UID URL, as the URL automatically appears as a result of the recording.
Steps to Get Verifiable Credential
Here are the steps required to get a Verifiable Credential (VC). The VC serves as a digital proof that users can use to verify their identity without disclosing excessive personal data.
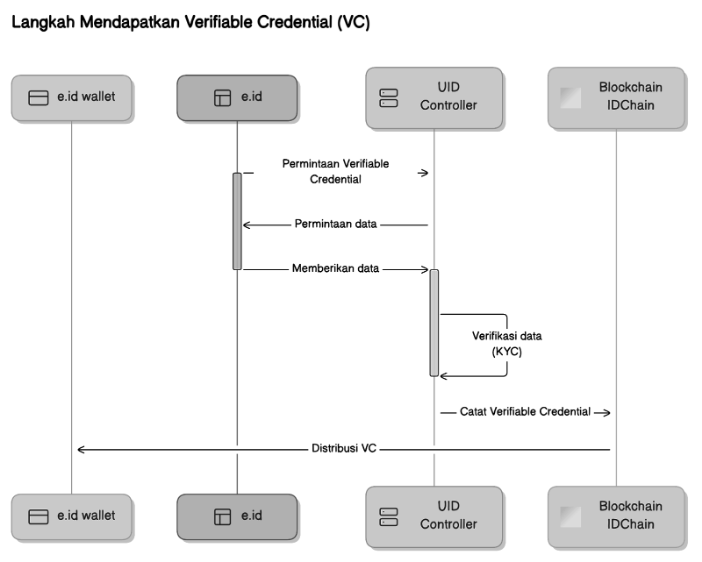
Diagram Explanation:
-
Request for Verifiable Credential through e.id
- Description: After the request is received by e.id, it is forwarded to the UID Controller. e.id acts as a bridge between the user and the UID system to ensure that the request is sent to the entity that can process it.
- Visual Representation: An arrow from e.id to the UID Controller indicates the submission of the request for processing.
-
Data Verification by UID Controller
- Description: UID Controller receives the VC request and verifies the user's data. At this stage, the UID Controller may ask the user to provide additional data necessary for the verification process. This often involves a KYC (Know Your Customer) process to ensure the authenticity of the information provided.
- Visual Representation: An arrow labeled "Data Request" from the UID Controller to e.id shows that the UID Controller is requesting additional data for verification. An arrow labeled "Providing Data" back from e.id to the UID Controller indicates that the user is supplying the requested data.
-
Recording Verifiable Credential on the IDCHAIN Blockchain
- Description: After the data verification is successfully completed by the UID Controller, the Verifiable Credential (VC) is recorded on the IDCHAIN Blockchain. This recording ensures that the VC is secure, decentralized, and can be verified by third parties without altering the data.
- Visual Representation: An arrow from the UID Controller to the IDCHAIN Blockchain indicates the recording of the VC on the blockchain.
-
Distribution of Verifiable Credential through e.id Wallet
- Description: Once the VC is successfully recorded, the UID Controller sends the VC back to e.id, which then distributes it to the user's e.id Wallet. This way, the user has full access to the VC that they can use for various purposes, such as proving their identity or specific claims.
- Visual Representation: An arrow from the UID Controller to e.id, and then from e.id to the e.id Wallet, shows the distribution of the VC to the user.
Integration with Applications
The UID Protocol allows for easy integration with various applications through the APIs and SDKs provided by IDCHAIN. Here are the integration steps:
-
Using the UID API
- UID Creation: An endpoint for creating a new UID based on user data.
- UID Verification: An endpoint for validating an existing UID.
- UID Update: An endpoint for updating UID metadata.
-
API Key Registration
- Developers must register and obtain an API key to access IDCHAIN.
- This key is used to authenticate all requests to the system.
-
Using the IDCHAIN SDK
- IDCHAIN provides an SDK to facilitate developers in integrating the UID Protocol into their applications.
- This SDK includes functions such as UID creation, Verifiable Credential management, and identity verification.
-
Data Security
- All API connections use TLS to ensure that data does not leak during transmission.
- Sensitive user data is protected with end-to-end encryption.
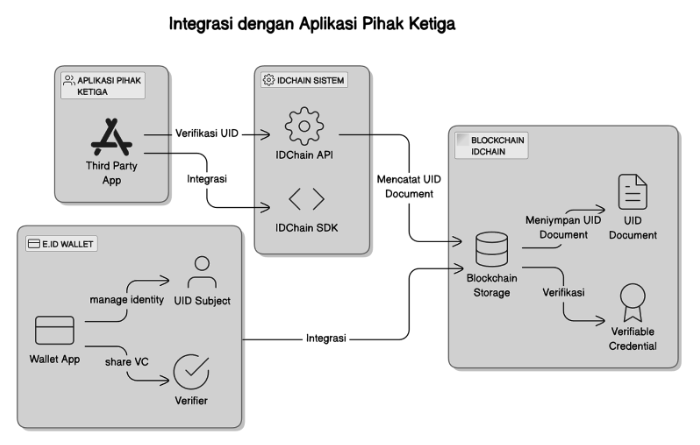
Diagram Explanation:
-
Third-Party Applications
- Description: This application is an entity that wants to utilize the UID Protocol, such as financial services, government services, or other digital services. They require user identity verification to provide access to their services.
- Relation:
- Third-Party Applications → IDCHAIN API: Third-party applications send requests for verification or access to UID through the IDCHAIN API.
- Third-Party Applications → IDCHAIN SDK: The SDK is provided to facilitate the integration process into applications without needing to understand the technical details of the blockchain.
-
IDCHAIN API
- Description: This API is an interface that allows third-party applications to communicate with the IDCHAIN system. The API receives UID-related requests from third-party applications and interacts with other components to fulfill those requests.
- Relation:
- IDCHAIN API → IDCHAIN Blockchain: Records the UID Document to the IDCHAIN blockchain to maintain its authenticity.
-
Blockchain IDCHAIN
- Description: The IDCHAIN blockchain is where UIDs and UID Documents are permanently stored. The blockchain guarantees the security, integrity, and transparency of the stored identities.
- Relation:
- IDCHAIN Blockchain → UID Document: The UID Document is stored on the blockchain to ensure it is immutable and can be verified.
- IDCHAIN Blockchain → Verifiable Credential: The UID Document is also used to create Verifiable Credentials (VC), which can be verified by third parties.
-
SDK IDCHAIN
- Description: This SDK is provided to assist third-party application developers in integrating the UID Protocol without needing to understand the technical details of the IDCHAIN blockchain.
- Relation:
- Third-Party Applications → IDCHAIN SDK: The SDK allows third-party applications to access the main UID functions in a simple and more efficient way.
-
e.id Wallet
- Description: The e.id Wallet is a tool that allows users to manage their UIDs and Verifiable Credentials. Users can easily check their identity and use their UIDs through this application.
- Relation:
- e.id Wallet → UID Subject: The e.id Wallet is the main interface for the UID Subject to access, verify, and manage their digital identity.
- e.id Wallet → Verifier: Users can also use the e.id Wallet to share Verifiable Credentials with the Verifier for verification purposes.
- e.id → IDCHAIN Blockchain: Makes requests for data related to UID Documents and Verifiable Credentials associated with the user's wallet.
Using UID in IDCHAIN
UID in IDCHAIN can be used for various digital identity needs, ranging from verification to transactions. Here are some examples of its usage:
-
Identity Verification
- Third-party applications can request users to provide their UID.
- The system will verify the UID using the blockchain to ensure its authenticity.
-
Secure Transactions:
- UID can be used as a unique identifier in transactions that require user identification.
-
Access to Digital Services:
- With UID, users can log into various digital platforms without needing to use passwords.
-
Verifiable Credential:
- UID combined with VC allows users to prove specific claims, such as membership or certification, without disclosing personal information.