Introduction
Welcome to our documentation. Here you will find various information about our products and services. Be sure to explore each section of the table of contents in the sidebar to get more in-depth information.
Option
Document Purpose
This document aims to provide a comprehensive yet easily understandable insight into how the UID Protocol operates within the IDChain ecosystem and its benefits. It is designed not only to focus on technical aspects but also to address the broader needs of users, including developers, organizations, and individuals who wish to understand or utilize the UID Protocol.
Specifically, this document will:
- Outline the fundamental concepts of IDChain as a blockchain infrastructure for digital identity.
- Explain the UID Protocol, including its operation, data formats, and key components.
- Provide practical guidance on the implementation and use of UID in various scenarios.
- Present real-world case studies to demonstrate how this technology can offer solutions in an ever-evolving digital landscape.
By understanding this document, readers are expected to recognize the relevance of UID technology in everyday life while also grasping how to integrate it into their systems or applications.
Terminology and Definition
To assist readers in understanding this document, here are key terms that will be frequently used:
| Term | Definition |
|---|---|
| UID (Universal Identifier) | A unique blockchain-based identifier used for secure and verifiable digital identification. |
| DID (Decentralized Identifier) | A decentralized identity that allows individuals to manage their identities independently without relying on a central entity. |
| e.id Apps | An application designed to help users create, manage, and utilize Universal Identifiers (UID) and Verifiable Credentials (VC). This app acts as a digital wallet directly connected to the IDChain blockchain, enabling users to securely store their digital identities, share data selectively, and easily verify their identities. |
| UID Controller | An entity responsible for the creation, management, and updating of UIDs. |
| Verifiable Credential (VC) | A digital proof that can be verified to substantiate identity claims without revealing personal data. |
What is IDChain?
IDCHAIN is an innovative blockchain platform designed to address the challenges of managing digital identities in the modern era. Utilizing a Substrate-based architecture, IDChain integrates blockchain technology, the W3C Decentralized Identifiers (DID) standard, and the Universal Identifiers (UID) protocol. Its primary goal is to create a secure, decentralized, and reliable infrastructure for digital identities applicable across various sectors, including government, private enterprises, and individual users.
The platform is designed to support the vision of "Creating sovereignty and freedom of expression in the digital age", as stated in IDChain's vision. With a user-centric approach focused on privacy and self-management, IDChain empowers individuals to have full control over their digital data without relying on central authorities.
Key Features of IDChain
-
High Security and Privacy
- IDChain ensures that users' sensitive data remains secure and under their control. With a self-sovereign identity approach, raw user data, such as names or other personal information, is not directly stored on the blockchain. Instead, only validation data, such as encrypted hashes, is recorded, reducing the risk of data breaches.
- The platform employs the Blake2b 256-bit hashing algorithm, known for its efficiency in maintaining data integrity and security, while also supporting rapid validation processes for a smoother user experience.
-
Traceability and Transparency
- Every change or access to identity data is recorded on the blockchain, creating an immutable digital trail useful for audits and verifications.
- This transparency allows organizations or individuals to build greater trust among stakeholders.
-
Self-Managed Digital Identity
- Utilizing the W3C Decentralized Identifier (DID) standard, IDChain enables users to have complete control over their data. Users can specify who can access their data and in what context.
-
Speed and Technological Efficiency
- IDChain employs the Blake2b 256-bit hashing algorithm, which has proven to be fast and secure in processing data. This algorithm not only ensures data reliability but also accelerates identity verification processes, which is crucial for real-time applications.
-
Flexibility and Interoperability
- Supported by a Substrate architecture, IDChain can be easily integrated with other blockchains or third-party systems, providing developers with the flexibility to build applications on this platform without needing to rebuild the entire infrastructure.
Why is IDChain Needed?
In a world increasingly reliant on digital services, the need for secure and trustworthy identities has become more pressing. With emerging threats such as identity theft, data breaches, and a lack of privacy, IDChain emerges as a solution that enables users to manage their identities in a way that is:
- Secure: Utilizing encryption and blockchain technology.
- Decentralized: Data is not stored in a single central location vulnerable to attacks.
- Efficient: Eliminating the need for lengthy manual processes in identity verification.
The Role of e.id in IDCHAIN
As part of the IDChain ecosystem, the e.id application plays a crucial role in providing a user-friendly interface for users to interact with the IDChain blockchain. This application allows users to create, manage, and utilize their UID and digital credentials in a simple and efficient manner.
Key features of the e.id application include:
- Creation of UID and Verifiable Credentials
e.id enables users to create new digital identities directly linked to the IDChain blockchain. This process includes securely verifying data using encryption technology. - Storage and Management of UID
As a digital wallet, e.id securely stores users' UIDs and provides full control over that identity data, including determining which parties can access it. - Selective Data Sharing
Users can use e.id to prove identity claims (e.g., age, citizenship, or employment status) without disclosing other irrelevant information. - Integration with Third-Party Services
With built-in API and SDK support, e.id simplifies the use of UIDs across various digital platforms and services such as banking, healthcare, or government. - Advanced Security and Privacy
All data in e.id is protected by the Blake2b hashing algorithm and blockchain-based encryption, ensuring that user data remains safe from external threats.
With the e.id application, IDChain provides a comprehensive ecosystem for managing digital identities that is not only secure and transparent but also user-friendly for individuals and organizations alike.
What is the UID Protocol?
The UID Protocol is a digital identity system designed to provide a unique identification for individuals, organizations, or other digital entities. Based on the W3C Decentralized Identifier (DID) standard, this protocol supports the management and verification of identities in a self-managed and decentralized manner. This means users can have full control over their identities without relying on third parties such as governments or financial institutions.
How the UID Protocol Works?
The UID Protocol utilizes a unique identifier, the UID (Universal Identifier), which serves as a digital representation of an individual or organization's identity. The UID acts as a key to securely and efficiently access various digital services. The process includes the following steps:
-
UID Creation
The UID is created by an entity known as the UID Controller based on information provided by the user. This process includes data validation to ensure the authenticity of the information. -
Recording on the Blockchain
Recording on the Blockchain Once the UID is created, it is recorded on the IDChain blockchain. This adds an extra layer of security as the UID becomes immutable and transparent for verification. -
UID Distribution
The recorded UID is then sent back to the user through the e.id application. Users can utilize this UID for various purposes, such as logging into applications or proving their identity in specific services.
Key Functions of the UID Protocol
- Creating Secure Digital Identities
UIDs are not only used to identify users but also act as non-falsifiable identifiers. This is crucial in scenarios such as identity verification for financial services or e-commerce. - Supporting Instant Verification
Through the use of Verifiable Credentials (VC), this protocol allows users to prove specific claims, such as membership status or professional licenses, without disclosing other sensitive details. - Enhancing Privacy
The UID Protocol is designed with the principle of minimal disclosure, meaning only relevant information is shared during the verification process. - Global Interoperability
By supporting the W3C DID standard, this protocol can be adopted across various platforms and ecosystems without requiring significant changes to the infrastructure.
Advantages of the UID Protocol
- Creating Secure Digital Identities UIDs are not only used to identify users but also act as non-falsifiable identifiers. This is crucial in scenarios such as identity verification for financial services or e-commerce.
- Supporting Instant Verification
Through the use of Verifiable Credentials (VC), this protocol allows users to prove specific claims, such as membership status or professional licenses, without disclosing other sensitive details. - Enhancing Privacy
The UID Protocol is designed with the principle of minimal disclosure, meaning only relevant information is shared during the verification process. - Global Interoperability
By supporting the W3C DID standard, this protocol can be adopted across various platforms and ecosystems without requiring significant changes to the infrastructure.
Benefit of the UID Protocol in Real Life
- Rapid Identity Verification
Users can prove their identities in services such as banks, schools, or other digital platforms without lengthy manual processes. - Reduction in Operational Costs
Organizations adopting the UID Protocol can reduce costs typically spent on manual identity verification or additional security systems. - Easy Access to Digital Services
UID allows users to access various services with a single unique identifier, eliminating the need to remember multiple passwords or carry physical documents.
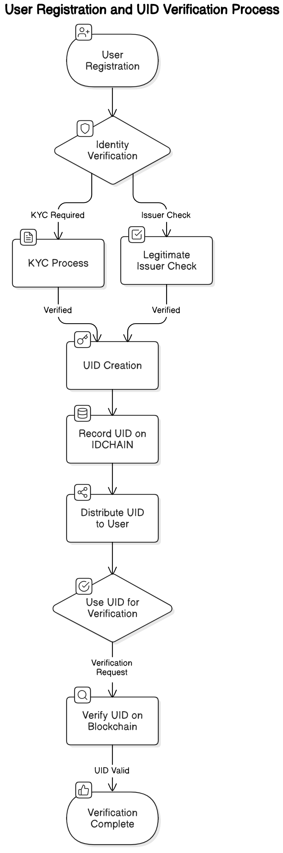
Flowchart Explanation:
- User Registration: New users register through the e.id app or third-party applications that support IDCHAIN.
- Identity Verification by UID Controller: The registered user data is verified by the UID Controller. This may involve a KYC (Know Your Customer) process or checks by a legitimate issuing entity.
- UID Creation: Once verification is successful, a unique UID is generated for the user. This process is carried out using cryptographic hash algorithms to ensure uniqueness.
- Recording UID on the IDCHAIN Blockchain: The created UID is recorded on the IDCHAIN blockchain. This recording guarantees the security, integrity, and immutability of the user's identity data.
- Distribution of UID to Users: After the UID is recorded on the blockchain, it is distributed back to the user through the e.id app or third-party applications.
- Using UID for Verification: Users utilize the UID for various purposes, such as identity verification in specific services. This process involves a Verifier who verifies the UID directly on the blockchain to ensure its authenticity.
- Verification Complete: Once the verification is successful, the Verifier can confirm that the user's identity is valid without accessing any other sensitive information.